Azure Active Directory Identity Provider
These are the general requirements for running Azure AD as an Identity Provider:
- An Azure Active Directory Premium P2 or Enterprise Mobility + Security E5 subscription
- Planning Space client users must add the following URL to Internet Explorer’s Intranet Zone to enable SSO: 'https://autologon.microsoftazuread-sso.com' (see the Microsoft Seamless SSO documentation)
- All firewalls must be configured to allow user login via Azure, and to allow SAML tokens to traverse from Azure to all of the Planning Space IPS servers.
The following diagram shows the basic authentication architecture supported by Planning Space. Azure AD does offer more complex topologies: Multiple Azure tenant federation, and Azure B2B which allows guest and other non-company access to Planning Space.
Azure AD authentication flow
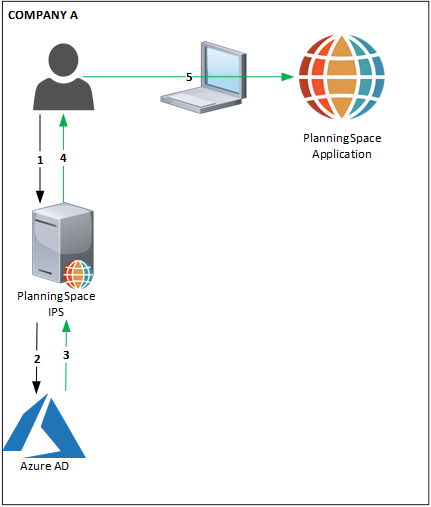
Azure Active Directory authentication architecture.
Initial authentication flow (numbers refer to the numbered arrows in the diagram):
- A user initiates login to the Planning Space tenant website, https://{IPS.domain}/{TENANTNAME} .
- IPS Server redirects to the Azure AD login page, where the user will enter credentials.
- Azure AD authenticates the user and passes a SAML token to IPS Server (containing the user's UPN).
- User has completed authentication for IPS and can access the tenant website. From here she can download the Planning Space client application to her local machine.
- User does login to the Planning Space client application. All subsequent activity takes place within the client application.
