Users
To access user account management, click Security in the Navigation menu, and Users in the Security top menu.
Note: You can only access this screen if you are logged in as an Administrator user, or if you are using a user account which is granted the role 'Security/Security'.
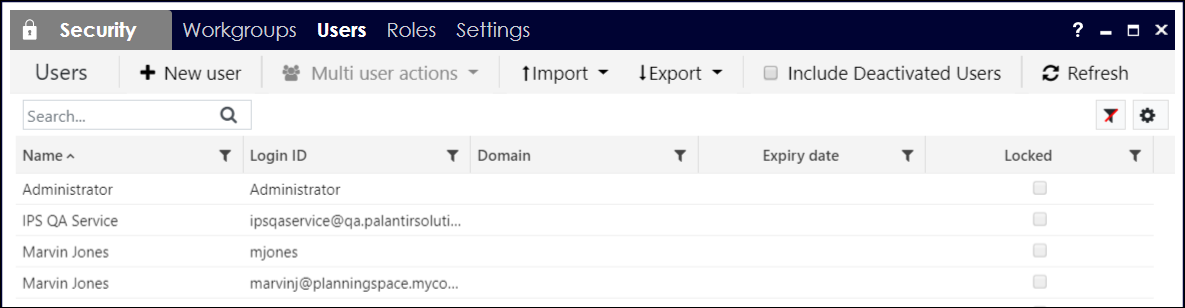
You will see the name, Login ID, and status information for the existing users for the tenant. Check the Include Deactivated Users box to show deactivated user accounts. (But note: the 'Locked' and 'Deactivated' checkboxes cannot be edited in this screen.)
Click any of the column headings to change the sort order of the list of users. The displayed users can be filtered by using one or more of the filter controls located at the head of each column.
Workgroups and Roles
Each user account can be granted (or denied) permissions to Planning Space data and functions by granting membership of different Workgroups, with each workgroup being allowed or denied access to different Roles.
For tenant and application administration, 'Administrators' is the default workgroup for granting 'god' administrator user rights. By creating new workgroups mapped to specific roles, for the different Planning Space applications, you can create fine-tuned administrative permissions.
User account types
There are three types of user accounts, based on different authentication methods, and not all of which may be enabled for use in your Planning Space deployment. An ordinary user should be provided with the appropriate login credentials by their local Planning Space administrator. Note there are no system functions for an ordinary user to recover access to their account in case of a problem.
| User Account Type (Authentication Method) | Required minimum configuration to create an account | 'Sign in' username for PlanningSpace | Comments |
|---|---|---|---|
| Local | Login ID, Name, Description, Password | Login ID | Password is stored and authenticated by the IPS Server. User credentials are passed from client to server over the HTTP/HTTPS network connection. |
| SAML2 | Login ID, Name, Description | Login ID | Requires an identity provider (IdP) service to be configured for claims-based OAuth2 authentication. See the Planning Space 16.5 Deployment Guide for more information. This is the recommended option for authentication in a production environment. The Login ID must be a valid UPN (User Principal Name) for the identity provider service. |
| Windows Active Directory | Login ID, Name, Domain, Description | Domain\Login ID | Authentication is performed by the IPS Server using the Windows Active Directory services. User credentials are passed from client to server over the HTTP/HTTPS network connection. This account type is mainly provided for compatibility with earlier versions of PlanningSpace. The Login ID must be a valid username for Windows Active Directory. |
For version 16.5 Update 13 and later: the allowed authentication methods - Local, SAML2, and Windows Active Directory) - can be enabled or disabled for each tenant independently by the IPS Administrator. The default is that all methods are enabled.
The disabling affects all interactive and API access for all user accounts of the specified type ('Local', 'SAML2', or 'Windows Active Directory'), and it includes API access using an assigned API key.
If Local method is disabled this will block logins for all Local accounts, including the default 'Administrator' user account.
When you add or edit a user account, a message will appear when the corresponding authentication method has been disabled: "This authentication method is currently disabled for the tenant. You will be able to save the user details however the user will not have login access."
Create a new user account
Click the New User button to open an edit pane for a new user account at the right-hand side. Use the Authentication Method selector to choose the account type 'Local', 'SAML2' or 'Windows Active Directory'.
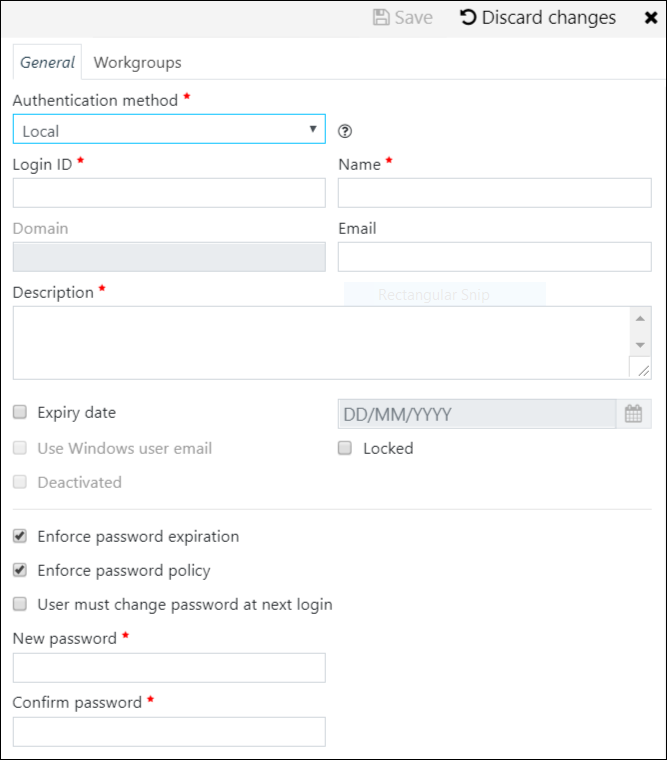
Different fields will be enabled/disabled depending on the account type. The fields marked with a red asterisk are required.
All user accounts require a Login ID (which is unique for the tenant), Name, and Description.
A 'Local' account requires an (initial) password to be input. Use the checkbox User must change password at next login to force the user to change the password. Use the checkbox Enforce password policy to force the password to always satisfy the policy on password complexity (see Security settings).
Expiry date: An account can be set to expire at a specified date (after which the user will not be able to login); a default value for that date can be set (see Security settings).
Click the Workgroups tab to set workgroup memberships for this account (see Workgroups).
Click the Save button to set up the new user account.
Automatic provisioning of SAML2 tenant user accounts
For version 16.5 Update 12 and later: Automatic provisioning of SAML2 tenant user accounts is possible based on the Identity Provider. This means that a new tenant user account can be created automatically when a user logs in to Planning Space for the first time using an account that is defined (and enabled to access PlanningSpace) by the Identity Provider's domain user services. It is also possible to dynamically-control the Planning Space user's membership of workgroups - by editing the user's domain account the Planning Space SAML2 account will synchronize whenever the user logs in to PlanningSpace. For configuration details see the Planning Space 16.5 Deployment Guide.
Edit a user account
To edit the settings for an existing user, click the user account name to open its edit pane.
The user account that is being edited will be highlighted in blue. Click the X button at the top right corner to close the edit pane.
There are two control buttons, which become activated when you have made an edit. Click the Save button to save the changes that you have made. Click the Discard changes button to undo any unsaved changes.
It is not possible to delete a user account, however it can be locked or deactivated (see below).
API key management
Users can generate and use an API key for access to the Planning Space APIs (see Generate API Key); this requires being granted the role 'Security/API Key' (note the role covers both generating, or re-generating, an API key and using it for API access).
When an API key is assigned to a user account this will be visible in the account's edit panel by the asterisks in the 'API key' field:

For version 16.5 Update 7 and later: API keys can be set to expire a specific number of days after generation (based on the value in the IPS setting 'API Key Lifetime'). The expiry date-time will be shown in the field API key expiration; the field will be blank if no API key exists for the user account, or it will display 'INFINITE' if the API key has no expiry date.
The stored key information for a user account does not change after the expiry date, therefore to determine if a user account has an active API key always requires a comparison of the expiry date-time with the current date-time.
The API Key value is not stored in Planning Space and therefore cannot be recovered by the user or by an Administrator. If an API Key value is lost, the user should generate a new key as a replacement.
The API key can be deleted in the account edit panel by clicking the Delete Key button. This will immediately revoke the user's API access. Also, an Administrator can immediately revoke or (temporarily) suspend the user's API access by removing the user's access to the 'Security/API key' role.
Multi-user actions
A number of actions can be applied simultaneously to multiple user accounts. These are:
- Lock or Unlock the accounts
- Change the Windows domain for the accounts
- Change the expiry date of the accounts
- Deactivate or Reactivate the accounts
- Assign or Unassign the accounts' membership of workgroups
- Change passwords or modify password policies for the accounts
- Delete the API Key for access to the Planning Space APIs
Use 'CTRL-Click' to select two or more accounts (they will be highlighted in blue) and this will activate the Multi user actions menu.
Export or Import user account information
Use the Export menu to export user account information as CSV data. Different information can be included; the options are Users (detailed user account data), Users & workgroups (all the workgroup memberships of user accounts), Users only in Everyone workgroup, and Workgroups without a user (the empty workgroups).
Note: The 'Users' export data contains entries for 'Last login date', 'Locked date' and 'Deactivated date' which are expressed in ISO 8601 date format of the form "{DATE}T{TIME}Z" where Z denotes UTC time zone and the time includes milliseconds digits. For example, "2021-01-04T14:35:44.293Z". (The ISO date format is not automatically handled by Microsoft Excel.)
You can import user account data using Import > Import from CSV (but this is not possible for 'Local' type accounts). Use Import > Download sample import file to get a template file. This provides a means to create user accounts as a batch process.
Note: If your user import data contains Unicode characters, please be aware that Microsoft Excel cannot write comma-separated plain text files with Unicode content. You can use the 'Unicode text' output format, which creates a file with tab separators, but you will need to have access to a Unicode-enabled text editor to substitute the tab separators with comma separators.
Lock or Deactivate a user account
Important: User accounts cannot be deleted, in order to preserve Planning Space tenant data for audit purposes.
The Locked state should be used to temporarily stop a user account being used for login. The Administrator can apply or remove the Locked state on user accounts. Locked state will be applied automatically when there are too many failed login attempts for a user account.
The Deactivated state should be used to permanently 'close' a user account. The account will not be visible in any live Planning Space operations, but the audit records of activities involving that account will be preserved. A Deactivated user account can be Reactivated.
