ADFS server setup
PAGE CONTENTS
IPS Manager has functions to generate (export) a 'Service provider' XML file that can be uploaded to the ADFS server, and avoid some manual configuration steps. Likewise, you can export an Identity Provider XML file from the ADFS server, which can be imported to IPS Manager (see Planning Space tenant IdP configuration).
Export Service Provider metadata in IPS Manager
In the IPS Manager 'Tenants' screen, go to the Identity Provider setting for the relevant tenant and click the 'Export metadata' button to create a file 'saml.xml'.
Export an ADFS token signing certificate
The token signing certificate is required for configuration of the Planning Space tenant.
How to export the certificate:
- Remote desktop to the ADFS server and open the ‘AD FS Management’ tool.
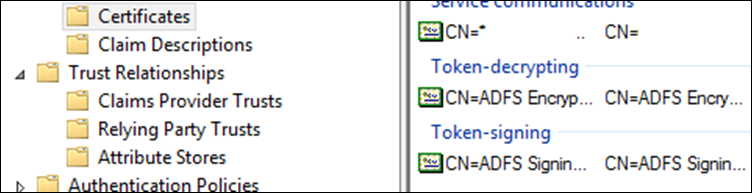
- Click 'Certificates' (under Service).
- Right-click 'token signing' and select the 'View Certificate'.
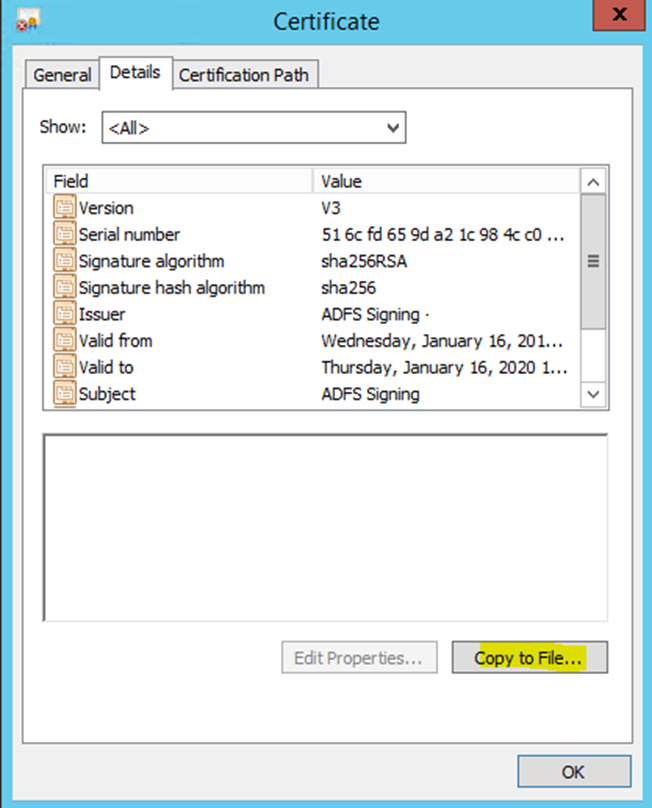
- Click the 'Details' tab and click the 'Copy to File' button.
- Click 'Next', then select ‘Base-64 encoded X.509’.
- Click 'Next, Save to a location, and close the wizard.
Configure an ADFS Relying Party Trust (using metadata)
- Remote desktop to the ADFS server and open the ‘AD FS Management’ tool.
- Add a new Relying party trust.
- Choose the option 'Enter data about the relying party from a file'.
- In the file location field, browse for the file 'saml.xml' that was created above.
- Click 'Next', and then click 'Finish'.
- Open the newly-created relying party trust by double clicking it (you may need to refresh first). Click 'Endpoints > Add SAML'.
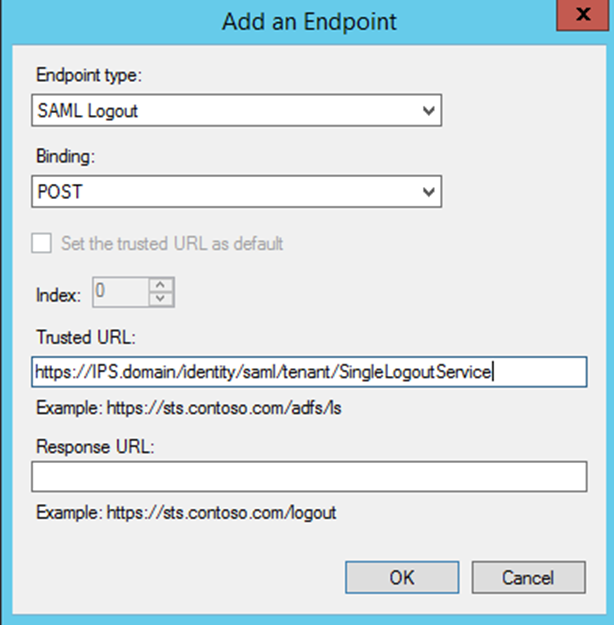
The Endpoint type is 'SAML Logout'. The Trusted URL is 'https://IPS.domain/identity/saml/tenant/SingleLogoutService' (with your own values for 'IPS.domain' and 'tenant' inserted). The endpoint path is case-sensitive and requires the case of the text 'identity/saml/tenant/SingleLogoutService' to be exactly as shown.
Manually configure the ADFS Relying Party Trust
For this configuration you will need a file containing an export of the IPS service address certificate.
- Remote desktop to the ADFS server and open the ‘AD FS Management’ tool.
- Add a Relying party trust.
- Choose the option 'Enter data about the relying party manually', and click 'Next'.
- Enter a display name. This will appear in the dropdown on the ADFS portal.
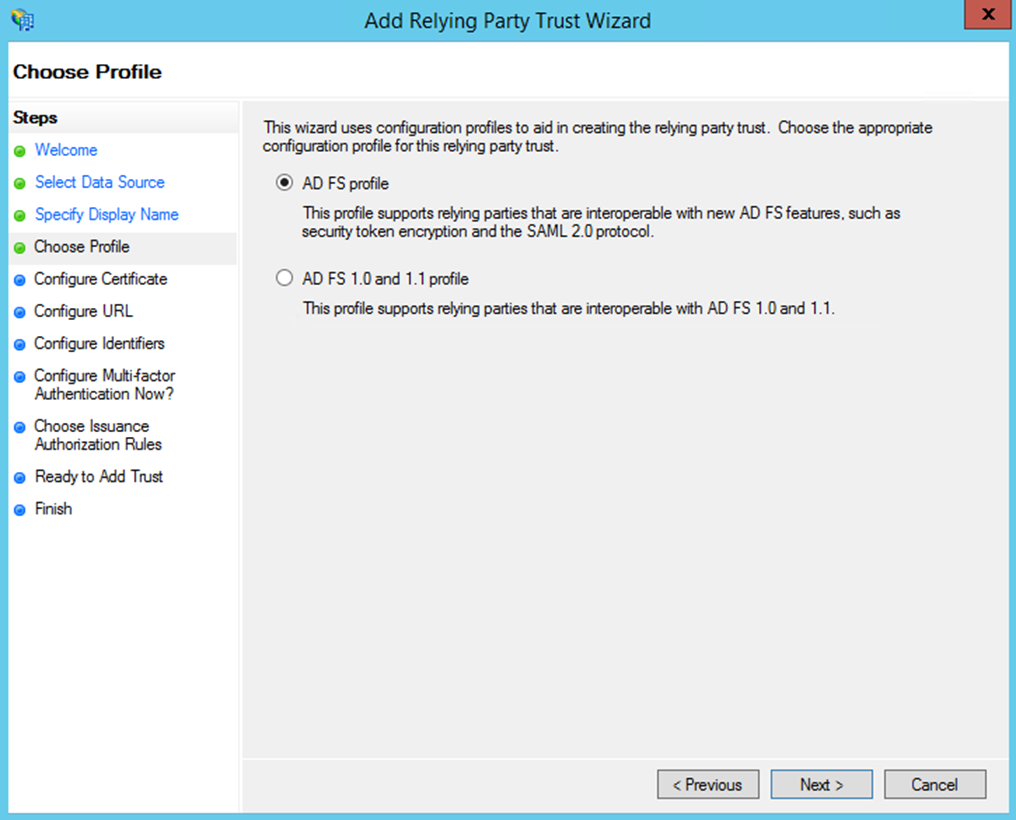
- Choose 'AD FS profile'.
- Click 'Next'.
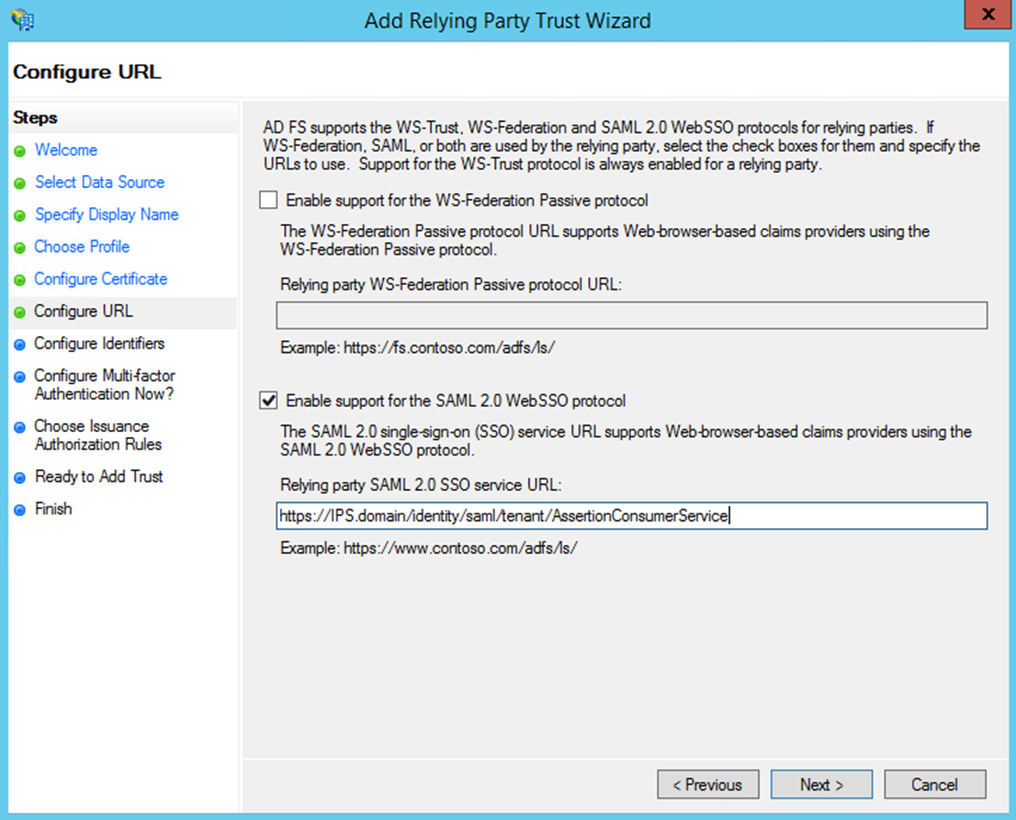
- Choose 'Enable support for the SAML 2.0 WebSSO protocol'. The endpoint address will be 'https://IPS.domain/identity/saml/tenant/AssertionConsumerService'. The segment 'IPS.domain' needs to contain the service address of the IPS Manager (for a cluster this is the address of the load balancer); 'tenant' should be replaced by the actual tenant name. The endpoint path is case-sensitive and requires the case of the string 'identity/saml/tenant/AssertionConsumerService' to be exactly as shown.
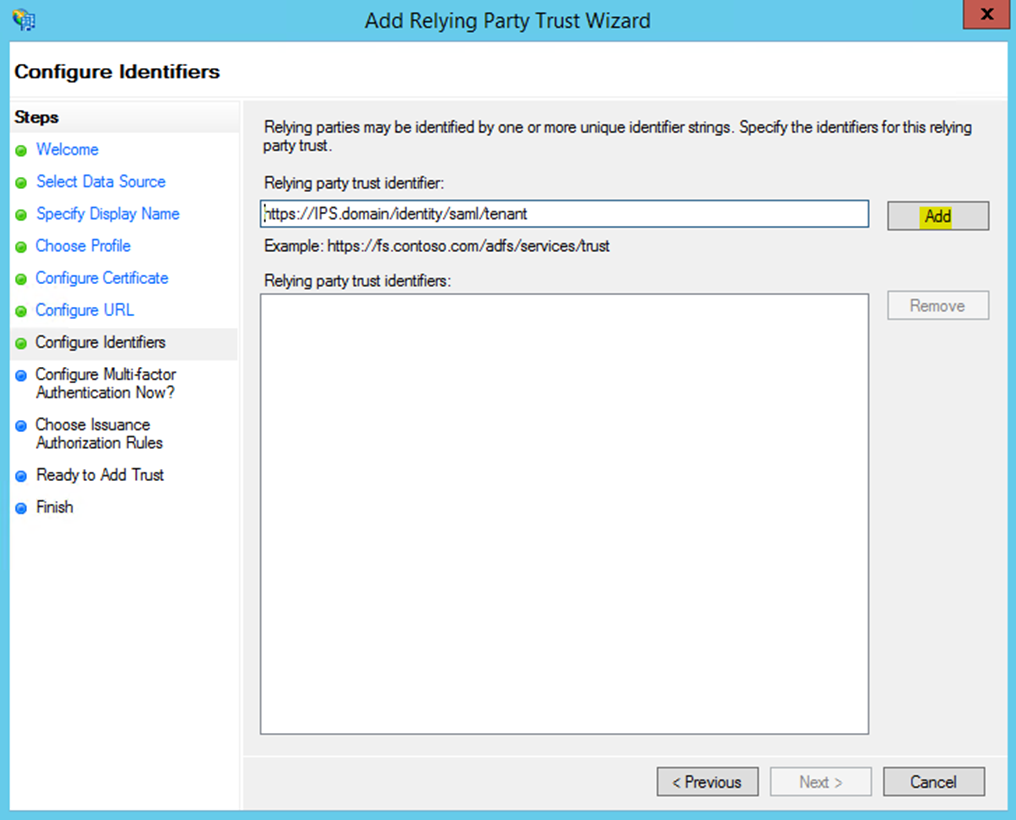
- Enter the relying party trust identifier. This is 'https://IPS.domain/identity/saml/tenant' (with your own values substituted for 'IPS.domain' and 'tenant'). The endpoint path is case-sensitive and requires the string 'identity/saml/tenant' to be all in lowercase.
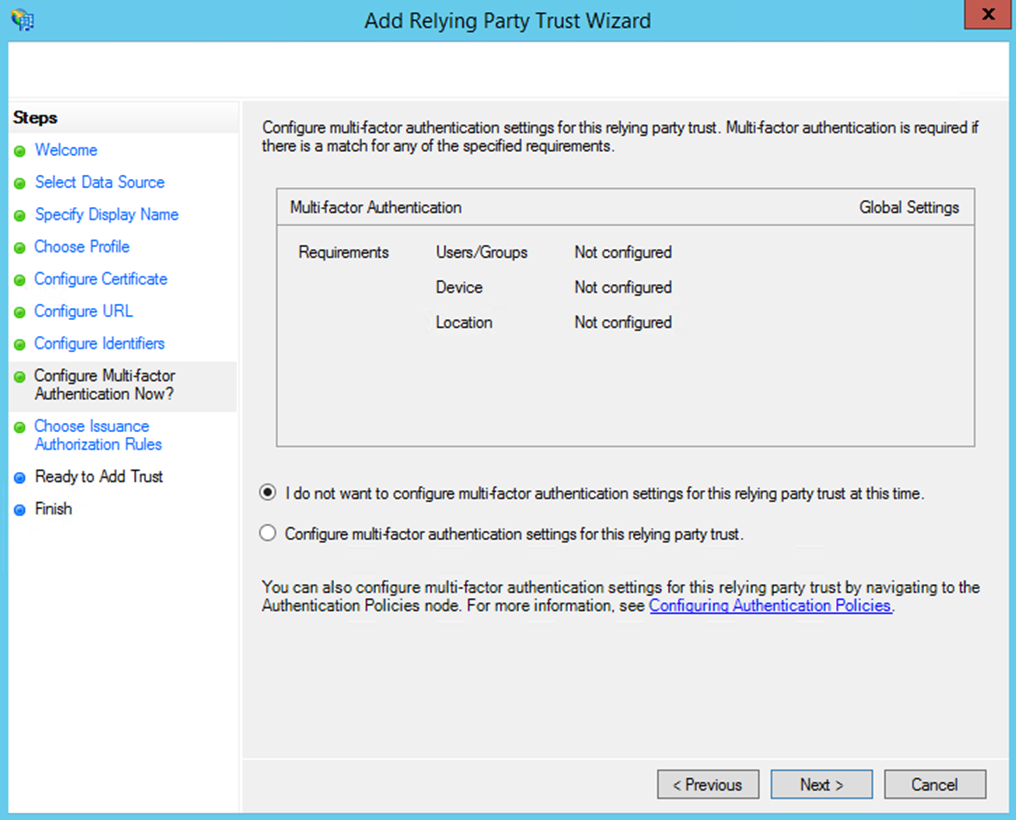
- Choose 'I do not want to configure multi-factor authentication'.
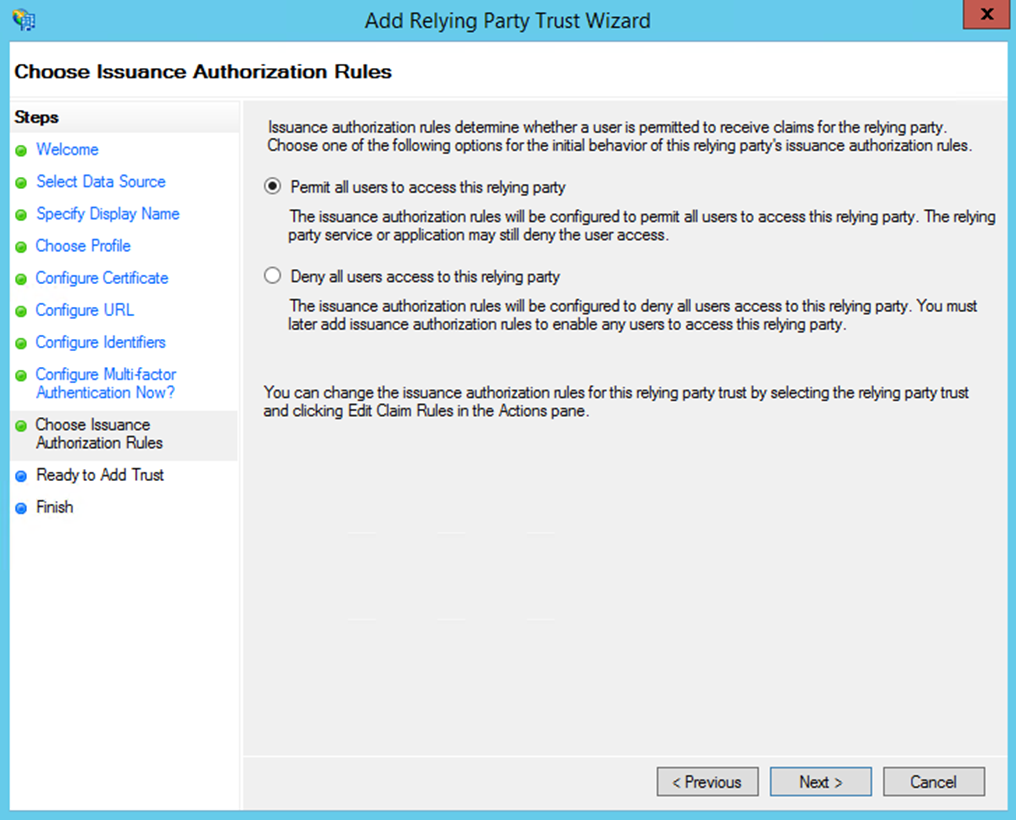
- Choose 'Permit all users to access this relying party' (the 'Deny' case is also usable, but it is an advanced-level configuration which is not explained here).
- Click 'Next', and the click 'Finish'.
- Edit the relying party trust you just created by double clicking it (you may need to refresh first)
- Click 'Endpoints > Add SAML'.
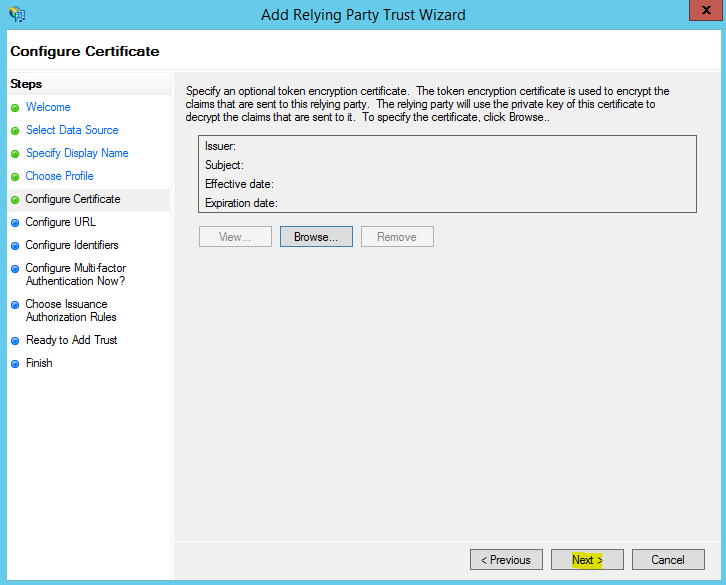
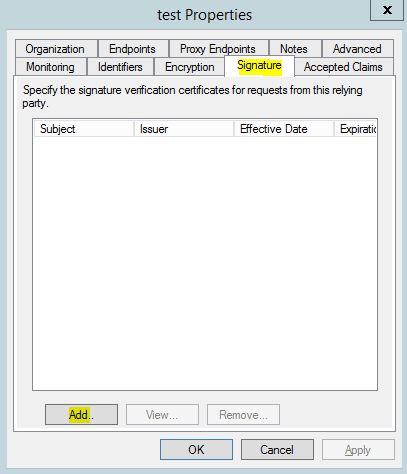
- Right-click the Relying Party Trust you've created. In the Properties dialog, select the Signature tab, and click the 'Add' button.
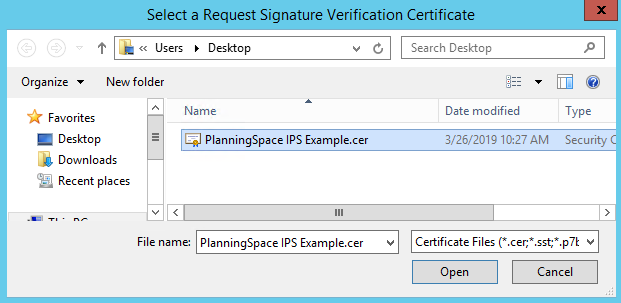
- Upload an exported version of the IPS service address certificate (use format Base-64 Encoded X.509).

The Endpoint type is 'SAML Logout'. The Trusted URL is 'https://IPS.domain/identity/saml/tenant/SingleLogoutService' (with your own values for 'IPS.domain' and 'tenant' inserted). The endpoint path is case-sensitive and requires the case of the text 'identity/saml/tenant/SingleLogoutService' to be exactly as shown.
Edit the claim rules
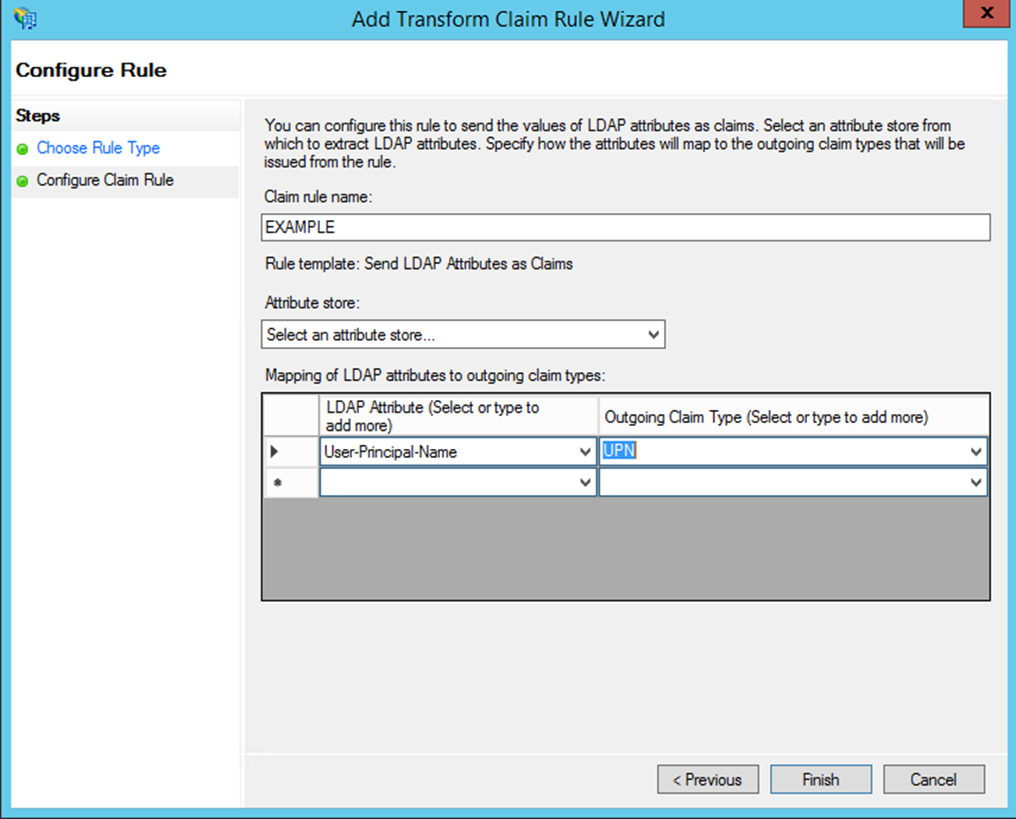
In the ‘AD FS Management’ tool, click 'Edit Claim Rules' for the relying party trust that you have created.
- Choose 'Send LDAP Attributes as Claims' and click 'Next'.
- Enter a name for the 'Claim rule name'. 'LDAP Attribute' is set to 'User-Principle-Name'. 'Outgoing Claim Type' is set to 'UPN' (i.e., the same as is used for the Planning Space tenant configuration).
SSO for the Planning Space application client
The Planning Space application client has a Chromium-integrated embedded browser. An additional configuration step is needed to allow single sign on once IPS has received the SAML token and authenticated the user. SSO will take the identity of the user launching the Planning Space application client, so this must be the same user which authenticated against IPS (via ADFS).
To configure SSO for the Planning Space application client you need to change the ADFS 'WIASupportedUserAgents' options.
Remote desktop to the ADFS server and open Powershell. Check the supported browsers by typing:
PS> Get-ADFSProperties | Select -ExpandProperty WIASupportedUserAgents
If 'Mozilla/5.0' or 'Chrome' are not listed, run one of the following commands, depending on preference:
PS> Set-AdfsProperties -WIASupportedUserAgents ((Get-ADFSProperties | Select -ExpandProperty WIASupportedUserAgents) + “Mozilla/5.0")
PS> Set-AdfsProperties -WIASupportedUserAgents ((Get-ADFSProperties | Select -ExpandProperty WIASupportedUserAgents) + "Chrome")
Then restart the ADFS service, and check the currently-supported Browsers by typing again:
PS> Get-ADFSProperties | Select -ExpandProperty WIASupportedUserAgents
