Okta Integration
Quorum-hosted instances of Execute support federated sign-on through Okta to simplify user sign-on, and user management.
This allows:
- Users to easily signin to Execute using domain credentials.
- Administrators to more easily manage offboarding users.
Setup
In most cases, the setup of integration between Execute and Okta will be handled by Quorum’s Application Delivery team as part of the setup/configuration of your environment. This will require Application Delivery and your IT department work together to link Quorum’s Okta instance, with your Active Directory controller.
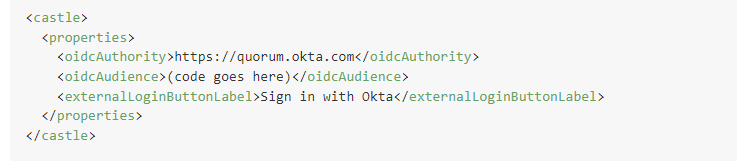
Once your domain has been federated with Okta, Execute needs to be configured to integrate with Okta. The configuration is managed in config/external_login.config and would look something like this:
Managing Users
Most user-management activities still happen within Execute.
- Adding / Removing users
- Assigning Administrative Privileges>
- Assigning User Privileges (create rights, approval rules, etc.)
Tying Execute to Okta serves two purposes:
- It enables user-login without requiring users setup/remember a separate password for Execute
- It ensures that users who are deactivated on the domain are unable to access Execute without requiring the user account in Execute be explicitly deactivated.
Users in Execute are linked to Okta based on the configured email address.
Okta-only Logins
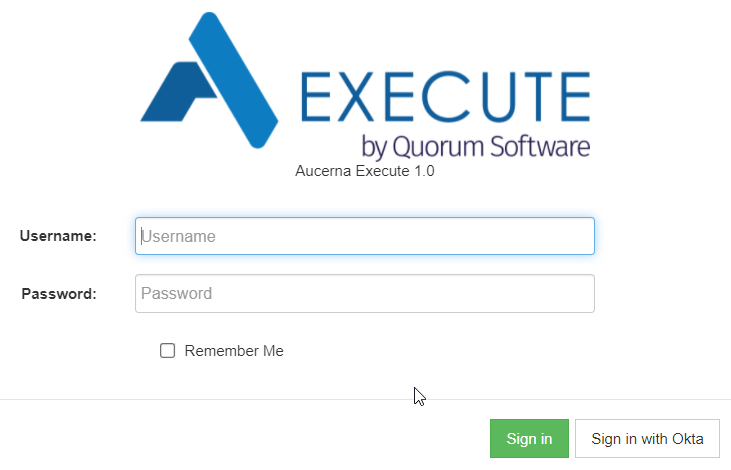
To simplify the login experience for end-users, it is possible to configure the Execute login screen to Okta-only mode. When configured in this way, the login screen will look like this:

To enable Okta-only mode, login as an Administrator and navigate to Tools > Configuration > Settings and change the value of Authentication Type to WINDOWS.

Mixed Logins (Okta and Password-based)
In some environments (common in TEST environments) it is important to be able to login with both federated and password-based logins.
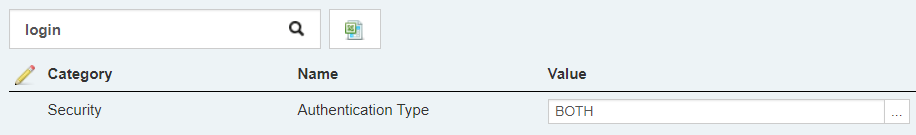
To enable mixed login mode, login as an Administrator and navigate to Tools > Configuration > Settings and change the value of Authentication Type to BOTH.
Troubleshooting
For the most part, the integration between Okta and Execute should be fairly simple and trouble free (assuming federation is correctly configured and the user is able to login to Okta successfully).
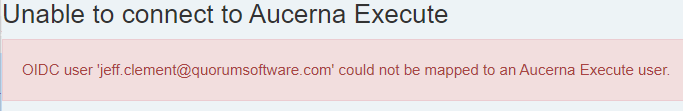
Upon an attempted login, the user might see the following message if their email address doesn’t map to a user account in Execute.
If the user’s email address maps to multiple user accounts in Execute, the user will see the following error.