Detailed information about pairing mobile devices with Execute
About Device Pairing and Remember Me
Execute’s Device Pairing and Remember Me functionality allows users to generate and store a device specific login to automatically log into Execute and avoid having to enter their username and password (re-authenticate) each time they login.
Both these features improve the user experience when following links to AFEs from email notifications.
This requires that the device be secure to the extent of corporate policy.
Remember Me

Click image to expand or minimize.
When logging into Execute with a user-account and password, rather than single-sign-on with Windows credentials, the user can choose to Remember Me.
The Remember Me feature will generate a random unique long-term device identifier (i.e. “0a8d1a6deac54220a05c3e13ede07db0”), associate it with the user’s account in Execute and store it in the web browser’s local storage. In this scenario data is hashed so that it is not available in a usable form in the database.
When the user re-connects to Execute in the future Execute will attempt to use the long-term identifier, if present, to login. If that is successful, the user will not see the login dialog. If the long-term identifier has expired or has been manually removed the user will be presented with the login screen and be required to re-authenticate.
This functionality is available on all browsers (desktop and mobile) when manually logging into Execute.
Device Pairing
Device pairing gives a way to generate and associate a long-term identifier with a device, without using the Remember Me feature. This is particularly useful where single-sign-on is enabled since single-sign-on will not work on mobile devices or devices that aren’t part of your domain.
- The device is on the same network / LAN as the Execute Service
- The device is external to the network but gains connectivity through a VPN or similar system
- The device is external to the network and Execute has been configured to allow connections from outside of the company network (i.e. proxy server / change of firewall rules)
Device pairing means that once the pairing is complete users of that device will not be required to authenticate to Execute. This greatly increases the usability of Execute on mobile devices but does not mean that we rely on the device’s security functionality for user authentication. For this reason it is important the devices are passcode locked or protected by another mechanism, such as Touch ID.
Pairing a Device
Device pairing is accessed with the Pair New Device screen under the Session button in the top right corner of the screen when logged into Execute.
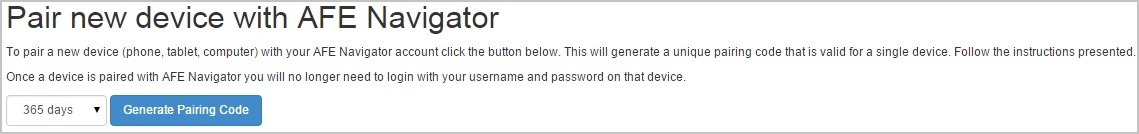
When creating a new pairing select the duration of the pairing and click Generate Pairing Code.
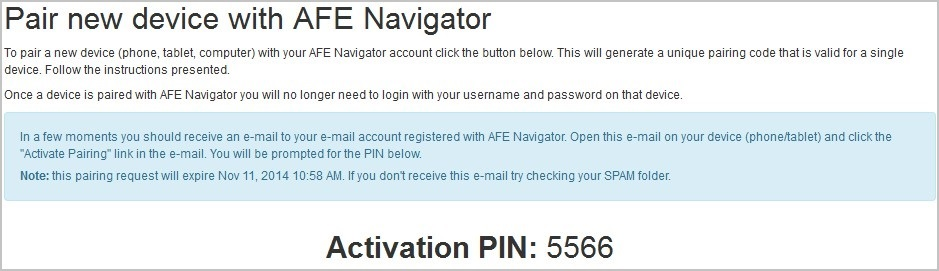
This will generate a new pairing link and is sent to the email account associated with that Execute username. The intent is that this makes it difficult for unauthorized users to pair devices with another account and is also a best effort approach to ensuring that paired devices are already receiving company email and meet a minimal security criteria. A pairing PIN is also generated and this must be entered on the device being paired in order to complete the pairing process.
Click image to expand or minimize.
The pairing email will contain a link that should be clicked on via the device being paired to Execute. Pairing requests are valid for 60 minutes before expiring. If a request expires the user will need to begin the process again.
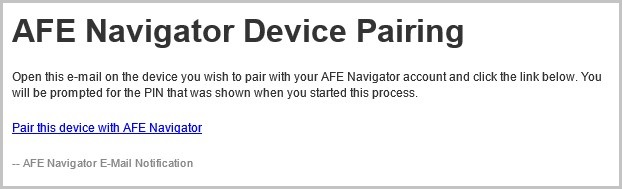
Once the user clicks the Pair this device with Execute link from their device they will see the Activate Execute Device Pairing screen. On this screen they will be required to enter the pairing PIN and a device description. The device description is useful for administration of long-term tokens if the device is later lost or compromised.
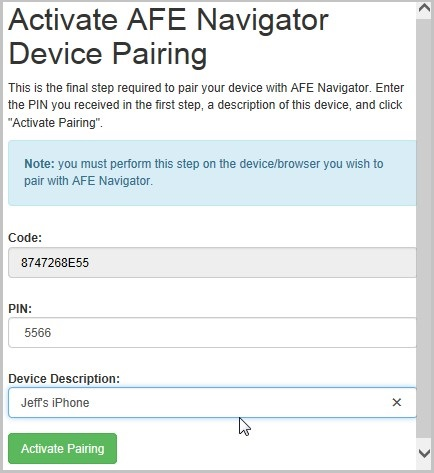
Click image to expand or minimize.
After user clicks the pairing link on their device and enters the correct pairing PIN a randomly generated unique longterm-token (i.e., “0a8d1a6deac54220a05c3e13ede07db0”) will be generated, associated with that user’s account in Execute and stored in the Local Storage for that device’s web browser. Once this is done the user will be able to seamlessly click links in email messages and follow those into Execute without re-authenticating.
Managing Long-Term Sessions
Both the Remember Me and Device Pairing features create long-term session tokens and associates those with the user’s Execute account.
These can be managed by the user within the Manage Long-term Sessions screen accessible under the Session button in the top right of their screen when logged into Execute.
The Manage Long-term Sessions screen will present a list of the user’s long-term tokens, what they are used for (mobile, hostname) and allow them to be manually removed. Removing a long-term token will render that token useless and prevent future automated login from that device.
In the case where a user’s device(s) are lost or compromised, and where it is not feasible to have the user login to remove these tokens, an admin with the ‘Manage User Sessions’ privilege can remove any long-term tokens via the Manage Long-term Sessions screen. This privilege allows an admin to remove any long-term tokens for any user at any time.
It is also possible to remove a long-term session via a SQL query such as this:
delete from longterm_sessions where
userid = (select userid from users where email = 'user@domain.com');
This query will remove all long-term tokens based on a specific email address.
This allows for creation of scripts which automatically expire sessions at an interval different from what Execute does by default.
Common Questions & Concerns
What is the strength of device-specific pairing token for authentication?
The device specific long-term token is 128-bit random token expressed in hexadecimal format (i.e. 0a8d1a6deac54220a05c3e13ede07db0). In 8.1 and beyond the token has been upgraded to a 256-bit random identifier. The token is intended to be long enough that brute force attacks against it are not feasible. Tokens are not shown to the user and are never reused between devices. This means that a compromised long-term token can be expired without affecting other long-term tokens for the user.
How are long-term tokens protected in the database?
The MD5 hash of the long-term token is stored in the database and the browser stored credential is hashed and compared with this stored hashed token. A user who has read-access to the LONGTERM_SESSIONS table will not have enough information to compromise a user account.
In Execute 8.1 and beyond the hashing algorithm has been changed to a more collision resistant SHA-256.
How are long-term tokens protected on the device / browser?
The long-term token is stored in the browser’s Local Storage and subject to whatever protection the browser offers. In general, this information is only accessible to Javascript running from the website that stored the data, in this case Execute. It is expected that the devices storing these tokens be secure to the extent required by corporate policy and that malicious software on the device itself is not a threat we can defend against. Malicious software on the device could also capture login credentials as they are entered.
We do recommend that devices storing long-term tokens are protected by a passcode or Touch ID to prevent unauthorized use of the device itself.
